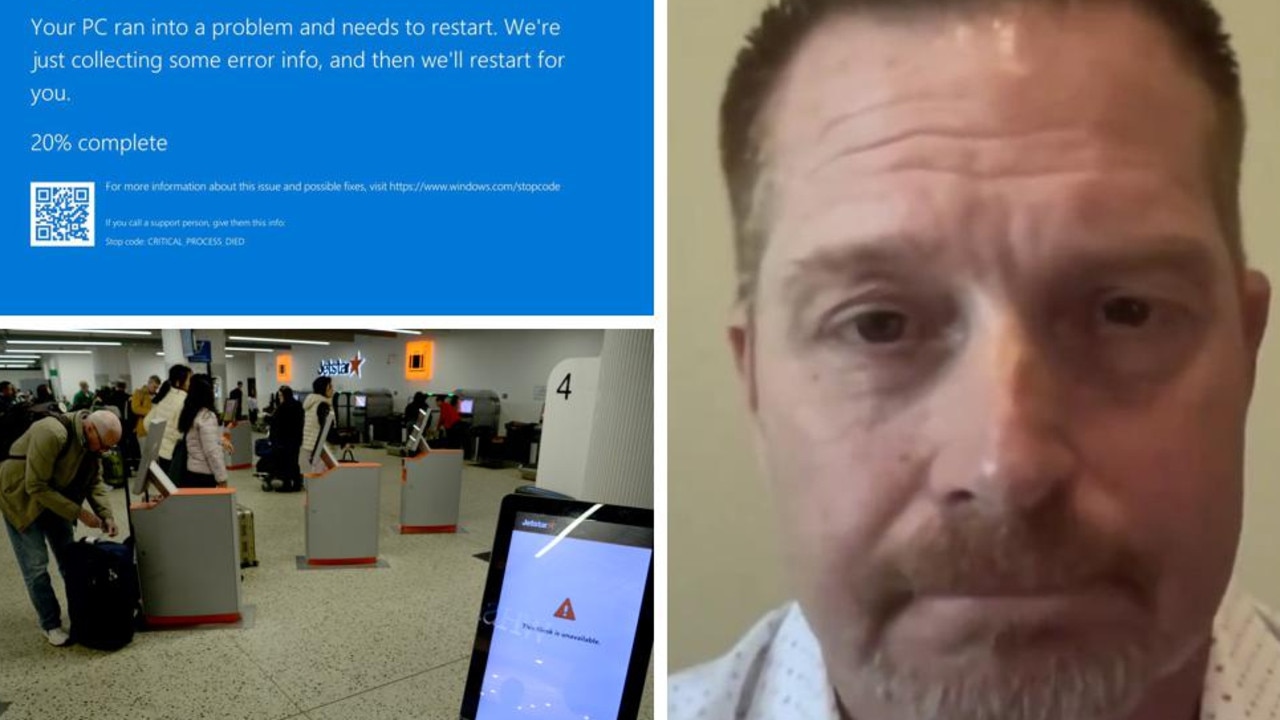
The company behind the flawed update that caused chaotic IT outages across the world has revealed a fix for the dreaded “Blue Screen of Death” that leaves computers stuck in a loop of restarts.
Computer systems across Australia were disrupted at around 3pm on Friday after a flawed driver update was released by US cybersecurity giant CrowdStrike.
All Microsoft systems were removed as a result.
Office workers and customers’ screens in places like supermarkets and airports have been repeatedly hit by the “blue screen of death” (BSOD), which causes computers to reboot and crash.
Airlines, banks, media companies, gas stations and other major businesses and retailers have all come to a halt as a result.
Mac and Linux hosts are not affected
In a statement, CrowdStrike said the company is actively working with customers affected by the flaw in the latest driver update.
They have confirmed that the outage was not caused by a malicious hack.
“The issue has been identified and isolated and is being addressed,” the company said Friday night.
“We recommend that organizations ensure they communicate with CrowdStrike representatives through official channels,”
The company has released a small technical fix for computers experiencing the BSOD:
CrowdStrike Troubleshooting for Computer BSOD
- Reboot the host to give it a chance to download the restored channel files. We highly recommend putting the host on a wired (not Wi-Fi) network before rebooting, as the host will connect to the Internet much faster via Ethernet.
- If the host crashes again, do the following:
- Boot Windows into Safe Mode or Windows Recovery Environment
- NOTE: Setting up the host on a wired (not Wi-Fi) network and using safe mode with networking may resolve the issue.
- Navigate to the %WINDIR%\System32\drivers\CrowdStrike directory.
- Windows recovery defaults to X:\windows\system32
- Go to the appropriate partition first (default is C:\), then go to the crowdstrike directory:
- C:
- cd windows_system32_drivers_crowdstrike
- NOTE: On WinRE/WinPE, navigate to the Windows\System32\drivers\CrowdStrike directory of the operating system drive.
- Go to the appropriate partition first (default is C:\), then go to the crowdstrike directory:
- Find and delete the files that match “C-00000291*.sys”.
- do not Delete or change other files or folders
- Cold boot host
- Shut down the host system
- Start hosting from off state
- Boot Windows into Safe Mode or Windows Recovery Environment
- Note: BitLocker encrypted hosts may require a recovery key.
CrowdStrike chief apologizes for disruption
CrowdStrike CEO George Kurtz told US television program Today that he was “deeply sorry” for the outage.
“Basically, the system was sent an update, which contained a software flaw and caused problems with Microsoft’s operating system,” Kurtz told the program.
“We quickly identified this issue and fixed it.”
Mr Kurtz clarified that the incident was not a cyber attack and was only caused by a faulty update.
“It may take some time for some systems to not be able to recover automatically,” he said.
Some systems have returned to normal, but the airport is still affected by cancelled flights due to the disruption.
Several planes were grounded at Sydney Airport on Friday and Saturday due to IT issues and strong winds.
Payments at Woolworths and Coles were also affected by the BSOD.
Home Affairs Minister Claire O'Neill has urged Australians to be wary of scammers amid reports an email claiming to be from CrowdStrike has been asking people for their banking details.
“Don’t give any details. If someone calls you and asks you to help me reboot my system, I’ll hang up,” she said.
“Then step back and think about it. Consider the text you just received and ask, ‘Does it make sense to you?’ Your bank will never ask you to enter your bank account details.
“If you have provided any personal information, please be sure to contact your financial institution and let them know you are concerned about any calls or emails you may have responded to.”